Computer-Mediated Communication
(CMC)
One-to-One CMC
E-Mail Basics:
@'s, Smileys, Angle Brackets, and Sigs
Tracking Down E-Mail (and Other) Addresses
Paddling Through the Patois:
Net Jargon
- E-mail's literal form is written language, but its tone is closer to speech.
- E-mail abbreviations, typographic conventions, and computer-speak patois
Common abbreviations in e-mail are:
BTW By The Way LOL Laughing Out Loud
GD&R Grinning, Ducking, and Running L8R [see you] Later
IMHO In My Humble Opinion FAQ Frequently Asked Questions
ROTFL Rolling On The Floor Laughing RTFM Read the Fucking Manual
Smileys or emoticons
Emoticons are punctuation marks that, when viewed sideways, resemble little
smiley faces
:)
:-) smiley with a nose :-O shock
Q:-) smiley with a beret :( sadness, disappointment
;) irony or flirtation (a wink) :] goofiness
:-p derision (tongue sticking out) 8-) smiley with glasses
See also, Dave Barry's emoticons,
from Dave Barry in Cyberspace. (Local mirror.)
Angle brackets (the greater-than/less-than
signs: <>) to indicate something akin to stage directions in a play.
E.g., humility might be suggested like this:
<digging toe in sand>
Thank you for the kind words in your last message.
Or, the thrill of discovery might be indicated like this:
<slapping forehead>
I think it would be fun to run a newspaper!
Internet equivalents to
underlining, italics, boldface, superscripts, or other common typographic conventions:
_Putting an underscore before/after a phase equals underlining._
Asterisks before/after a word indicate *emphasis* (as if it were
italicized or bolded).
ALL CAPITALS also signifies EMPHASIS, but USING ALL CAPS ALL THE
TIME IS LIKE SHOUTING AND IS DISCOURAGED IN E-MAIL.
Sign Your Messages with
a "Sig"
- Many e-mail systems will automatically append a signature (or sig) to every
message.
- Should be short (no more than five lines) and about 70 characters (or less)
wide.
My own sig flirts with these limitations:
Jeremy Butler
jbutler@ua.edu
ScreenSite http://www.tcf.ua.edu/ScreenSite/
Telecommunication & Film/University of Alabama/Tuscaloosa
Quoting a Message
- When replying, it's good to quote a small portion of a msg to give the
context of your reply
- Don't quote more than is necessary
- Often > signs ("angle brackets" or "greater-than signs") are used to
signify quoted material
>Tried to run NS Nav 3 on my office's Mac computer. Someone else
did the
>installation. It crashes the entire machine when you load it. KER-blooey!
> Any idea what the prob is?
How e-mail works
- Networked computers exchange messages--actually just data in packets
- The information at the top of the message, before the body of it, is known
as the header
- Hidden in some e-mail systems
- In Pine, HdrMode reveals the full headers
- Which indicates the route the message took to get from one point to
another as well as other information about how the message should be handled
- E.g., the header from a message from Mary Beth Haralovich, chair of Media
Arts, to my mailbox in Alabama--which we may dissect line-by-line
- Received: from SpoolDir by TCF_NET (Mercury 1.30); 15 Jul 97 10:07:11
CST
- Return-path: <mbharalo@U.Arizona.EDU>
- Received: from nevis.u.arizona.edu by tcf.ua.edu (Mercury 1.30) with
SMTP; 15 Jul 97 10:07:08 CST
- Received: from localhost (mbharalo@localhost) by nevis.u.arizona.edu
(8.8.5/8.8.5) with SMTP id IAA41376 for <jbutler@ua.edu>; Tue,
15 Jul 1997 08:58:04 -0700
- Date: Tue, 15 Jul 1997 08:58:03 -0700 (MST)
- From: Mary Beth Haralovich <mbharalo@U.Arizona.EDU>
- To: Jeremy Butler <jbutler@ua.edu>
- Subject: Lunch for Guests?
- Message-ID: <Pine.A32.3.93.970715085510.29142K-100000@nevis.u.arizona.edu>
- MIME-Version: 1.0
- Content-Type: TEXT/PLAIN; charset=US-ASCII
- MIME = Multipurpose Internet Mail Extensions
- SMTP = Simple Mail Transfer Protocol
- ASCII (pronounced "as-key") = American Standard Code for Information
Interchange
- Messages are stored on these computers and may be accessed two ways:
- User connects his/her local, client computer (the one sitting
in front of them) to the storing or host or server computer
and reads the messages that are stored there--while maintaining the
connection between the two. (Remember:
most of the Internet is based on the client-server model.)
- Messages remained physically stored on the host computer (until
the user deletes them).
- E.g., using Telnet client to read your bama.ua.edu
mail using Pine; which is actually running on the distant machine
and is just being shown to you.
- User connects to the message-storing computer, transfers the
messages to his/her client computer from the host and then breaks the
connection.
- He/she may then read, respond, and/or compose new messages while
disconnected.
- Although there are several ways to do this, the most common is
POP3 (Post Office Protocol Version 3)
- An e-mail client contacts a POP server and moves the messages
from the distant machine to the local one (the one sitting in
front of the user)
- But, this only works for receiving messages, to send
them out you must use a different type of server computer--one that
provides SMTP (Simple Mail Transfer Protocol)
- An e-mail client contacts such an SMTP server and moves the
messages from the local machine to the distant one, which then
takes care of distributing them across the Internet.
- User connects to message-storing computer, and the user chooses
either to transfer msgs or not!
- IMAP (Internet Message Access Protocol)
- Allowing a client to access and manipulate electronic mail messages
on a server. It permits manipulation of remote message folders (mailboxes),
in a way that is functionally equivalent to local mailboxes.
Attachments and Related
Problems
- Attachments are files attached to the main part of the message
- Attachments are a common source of viruses
- E.g., the Melissa virus
- Spread via an attached MS Word document (a macro-based virus).
- When the attachment is opened (not when the message is read), it
reads the user's e-mail address book and sends itself out to 50 more
people.
- Also corrupts files on your harddrive.
- If the minute of the hour matches the date (for example, 3:31
on March 31), Melissa will insert the following Bart Simpson quote
into the current open Word document: "Twenty-two points, plus
triple-word score, plus fifty points for using all my letters.
Game's over. I'm outta here."
- Launched 3/26/99 and spreading incredibly quickly
- Melissa
timeline
- A significant antecedent to the "Love Bug" virus/worm
(May 2000)
- Materials sent through e-mail protocols must be totally, only ASCII
- Which makes attachments and non-English characters (like, ñ ) problematic
- But many e-mail clients have automated the whole process
- HTML Mail (aka "rich text")
- E-mail used to not allow any formating of text (e.g., italics,
boldface)
- More recent e-mail client software, however, uses HTML code to do so
- E.g., Netscape Messenger, MS Outlook Express, Eudora Pro
- Not only can text be formatted, but images can be included.
- The problem:
- If someone with an older e-mail program (like Pine) receives an HTML
message, it will be filled with extraneous garbage.
Free Web-based E-mail
Services
- Yahoo!, Hotmail, etc.
- Create your own e-mail service with ZZN
- Can be handy if you want an e-mail box that your boss/school does not own.
- Courts have said that employers own all the e-mail on their computer
systems. Thus UA has the right to read anything on yours!
Accessing Your Own E-mail
When You're Not at Home
- If you're away from your home computer, you may still be able to pick up
your e-mail.
- AOL Mail on the Web
- Connect to your AOL mail through a Web browser.
- MailStart
- MailStart and MailStart Plus work through a Web browser--any
Web browser anywhere. You fill in your e-mail address and password
and it collects your e-mail for you.
Many-to-Many CMC: Listserving
and Newsgrouping
Clerical Robots: LISTSERV,
Listprocessor, Maiser, and Majordomo
- An e-mail discussion list takes the basic principle of cc'ing and automates
it.
- Instead of a single human keeping a list of individual addresses and sending
e-mail to each of them, a discussion list is run by a computer a clerical
robot
- e.g., LISTSERV, Listprocessor, Maiser, and Majordomo
- 'Bot compiles the addresses and automates the distribution of messages.
Or, in other words, this clerical robot serves messages to a list of addresses.
It is thus generically a listserver.
- Listserving functions:
- Subscription
- Distribution
- Discussion threads
- Un-subscription
- Two separate functions with separate addresses:
- The listserving robot named Maiser, LISTSERV, Listprocessor, Majordomo,
etc.
- The group of subscribers.
Indexes and Digests
- Digest
- compiles the messages from a single day (or week),
- creates a list of the day's messages,
- and then sends the list and the messages themselves to the user in a
single e-mail package rather than message by message.
- Index
- Solely a list of messages for each day (or week) usually with
their subject headings and posters' names
- Does not include the messages themselves.
- Users may then request the specific messages in which they're interested.
|
Worldwide LISTSERV® statistics
(Wed, 20 May 1998)
|
| Number of public lists |
18,452 |
| Number of local lists |
61,130 |
| Total number of lists |
79,582 |
| Total membership (public+local) |
29,748,499 |
| Total messages delivered today |
26,397,893 |
| Total delivered using LSMTP™ |
13,877,964
(52.6% of total) |
Finding Lists
- CataList, the official
catalog of LISTSERV® lists
- Browse any of the 18,452 public LISTSERV®
lists on the Internet
- The List
of Lists
- Search through bazillions more lists--including ones that are not run
on LISTSERV®
- ScreenSite's listing of film/TV-related
discussion groups
Required Lists for TCF
389
- NewsScan
- TCF389@tcf.ua.edu
- Use your preferred e-mail account to send the following message
to maiser@tcf.ua.edu: subscribe TCF389
- Internet Tourbus
- Email LISTSERV@LISTSERV.AOL.COM with the message SUBSCRIBE
TOURBUS YourName
Use bamamail.ua.edu
(for UA accounts) or Web access to your preferred account and subscribe to these
three lists.
Usenet:
It's Kind of Like E-Mail, But Not Really
Usenet = bulletin boards in a hallway.
Newsgroups
- Messages in a newsgroup don't come to you, you must go find them.
- To read newsgroups, you must first connect your computer to another computer
that stores Usenet messages.
- These central computers all connect with one another and share the messages
that are posted to newsgroups.
Usenet Pointers
- Use a newsreader program or Netscape Navigator to access
newsgroups
- Newsgroups are arranged in hierarchies
- Read the FAQ's (Frequently Asked Questions) before posting
- Binary files and images may be attached to msgs using UUENCODE
- NS Nav and MS Internet Explorer encode/decode attachments for you
- Many Usenet resources have been collected at http://www.duke.edu/~mg/usenet/
A few film/TV newsgroups:
Cult movies alt.cult-movies
Stanley Kubrick alt.movies.kubrick
Steven Spielberg alt.movies.spielberg
SFX alt.movies.visual-effects
Martin Scorsese alt.movies.scorsese
Class newsgroups:
Forums are only
open to students enrolled in the class and are hosted by WebCT.
Instantaneous ("Real-Time")
CMC
- Chat Rooms and Channels
- Commercial Services (e.g., AOL) and Internet Relay Chat (IRC)
- One-on-one chat software
- ICQ and AOL
Instant Messenger


Previously limited to AOL members only, it now works with anyone on
the Internet. (Statistics as of July 1999.)
- "Internet Phone": Audio Over the Internet
- CUseeMe: Chat With Sound & Pictures
- Real-Time Audio/Video (one-way, streaming)
CMC Hazards
1. E-mail (In)Security
- At most locations, the computer system administrator or postmaster can
read any mail stored on that system.
- Moreover, as your mail travels an electronic route it can be read by just
about any system administrator along the way.
- Employers own company e-mail.
- Hackers/crackers may sniff for keywords like "VISA" or "password"
- Protect yourself with encryption
- Scramble your message using a specific key that you and your addressee
both know. When he/she receives the message, he/she uses the key to decrypt
it.
- Pretty Good Privacy (PGP)
- More on this later in the semester.
2. Flames and Flame Wars
- Rude or offensive messages attacking someone are known as flames
- May be used as a verb as well as a noun.
- The best treatment for flames is to extinguish them with the delete key.
To engage the enemy typically leads to a flame war (an escalating exchange
of flames), in which there are few winners.
3. E-Mail Fraud: Spam
and Fake Messages
One of my e-mail boxes
is very susceptible to spam. Here's a week's sample:
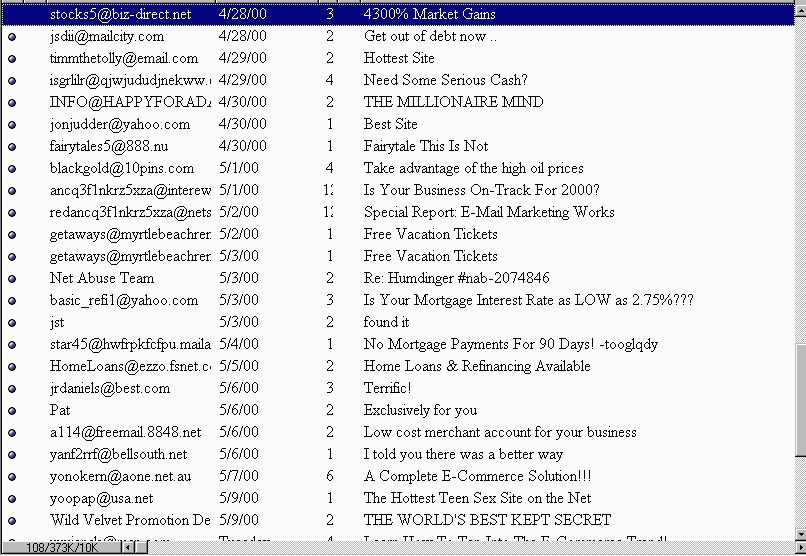
Examining the message
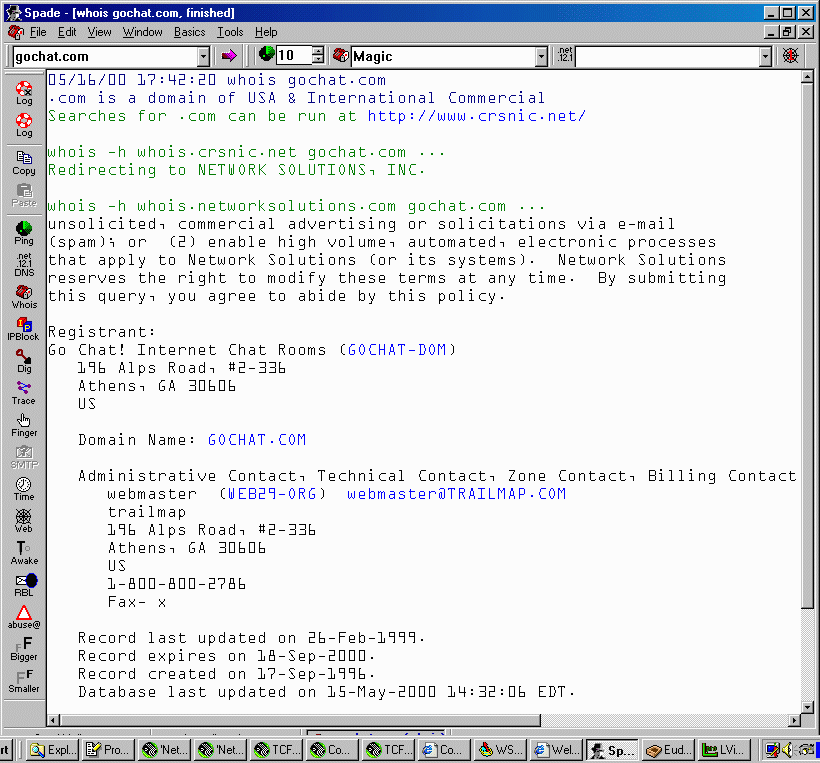
headers can often tell you where the message really came from. Sam Spade
software automates the process.

You can then track down
the contact persons for the real source.
How to deal with spammers
- E-mail the real mailer's postmaster or abuse person
- E.g., postmaster@interlinx.qc.ca
- E.g., abuse@aol.net or abuse@aol.com
- Look up real name of the company and contact them
- Doesn't always work
- A program such as Sam
Spade can automate this detective work.
- Just paste the entire header into it and it'll tell you where it really
came from.
- Do not reply to the fake address with a complaint
- Usually it'll just bounce back
- Sometimes spammers pick a real person's name as a way to harass them
- Some spammers use responses as as cofirmation that your address works
and increase the spam
- Some even ask for a reply, promising to take your name off their list,
but then just use it as a confirmation!
- Filter your e-mail
- Many e-mail clients will automatically delete messages with particular
subjects
- E.g., "!!!!!!!!" or "Sex" or "Make Money Fast"
- Or from particular locations
- E.g., Cyberpromotions--which is now (1998) out of business
4. E-Mail Obesity: Keeping
Your Mailbox Lean and Mean
- Squirrel away a copy of the list's instructions so that you might unsubscribe
quickly. It's a good idea to start a folder containing list instructions.
- If the volume of a list is too great, switch to a digest or index version
of it.
- Don't subscribe to more than one list at a time. Get a sense of how busy
a new list is before you add new ones.
- Review the list's archives to see how many messages are in it. SCREEN-L
and many other lists have archives that are available via e-mail, and/or the
World Wide Web.
- If you are having trouble with the robot, contact the human who maintains
it; but make an effort to resolve the problem on your own first. Otherwise,
depending on how harried the human is, you may be told RTFM.
- Sample the list's Usenet newsgroup (if one exists) to see how busy it is.
5. E-Mail Viruses and
Other Hoaxes
Computer viruses are a real and significant problem, but, currently,
you cannot catch one simply by reading an e-mail message.
However, you may be infected by opening an attachment
to an e-mail message. In fact, in 1999 e-mail became the most common way of
transporting viruses--bypassing the floppy disk as the most common carrier.

Most of these are "macro" or script viruses that live in Microsoft
Word documents. Never open a Word document--even from a friend--unless
you've been told, in advance, that it will be sent to you. Even then, you might
want to check with the person before opening it.
(The Melissa [March 1999] and Love Bug [May 2000] viruses masked themselves
as notes from friends.)
You can separate the hoaxes from the real threats by visiting:
6. Sexual (And Other)
Harassment in CMC
- Chat rooms and other instantaneous CMC can attract chowderheads whose sole
interest is to harass women. Some caution is advisable.
- Use a gender-neutral name
- Use the "bozo filtering" capabilities of your client software
- Most CMC software allows you to block messages from specific persons
Bibliography
- International Computer Security Association, Fifth
Annual ICSA Computer Virus Prevalence Survey: 1999.
Last revised: May 16, 2000 6:05 PM
Comments: jbutler@ua.edu





